Your computer’s RAM is still faster than even modern solid-state drives. RAM disks take advantage of this, using your computer’s RAM as a lightning-fast virtual drive. But you probably don’t want to use a RAM disk, anyway.
RAM disks are easy to sell — all you have to do is hold up performance benchmarks showing how much faster it is to read data from RAM than it is from even a fast SSD. But this isn’t the full picture.
What’s a RAM Disk?
To create a RAM disk, you would install a third-party program that creates a virtual drive in Windows. This program would reserve a section of your RAM — so if you had 4 GB of files in your RAM disk, the disk would take up 4 GB of RAM. All the files on your disk would be stored in your RAM. When you wrote to the disk, you’d just be writing to a different section of your RAM.
Initially, this seems like it could help optimize performance. If you installed programs in a RAM disk, you’d have near-instant load times because their data would already be stored in the fastest memory possible. When you save a file, it would happen almost instantly as it would just be copied to another portion of RAM. This would mean faster application load times and faster file read/write times for files saved in the RAM disk.
Why You Probably Shouldn’t Use One
However, there’s a big problem here. RAM is volatile memory. When your computer loses power, the contents of your RAM will be erased. This means that you can’t store anything important on a RAM disk — if your computer crashed because of lost power, you’d lose all the data in your RAM disk. So saving files to the RAM disk is pointless unless you don’t care that you’d lose the files — but if you didn’t care about the files, why save them in the first place?
Because RAM isn’t persistent, you’d also have to save the contents of your RAM disk to disk when you shut down your computer and load them when you turn it on. For example, let’s say you installed Photoshop to your RAM disk. You’d have to save an copy of your RAM disk to your computer’s hard drive to ensure you wouldn’t lose your Photoshop installation. You may want to do this automatically every few minutes or just at shut down.
When you turn on your computer, the RAM disk program would have to read the RAM disk image from your hard drive and load it back into RAM. In other words, you’re simply getting faster program-load times at the expense of longer boot-up times. Once your computer loads an application or other files form its hard drive, it caches them in RAM anyway — so it’s a bit silly to install an application or game in a RAM disk rather than on your hard drive. Either way, once you load the application, it will stay present in your memory for quick loading later.
RAM disks also reserve a good chunk of your memory, ensuring you can’t use it for anything else. Windows uses unused memory to cache files anyway, and it does it all automatically and in the background. If you need the memory for something, Windows will instantly discard the cached data. With a RAM disk, you’d have to shut it down manually to free up memory.
How You Would Make a RAM Disk
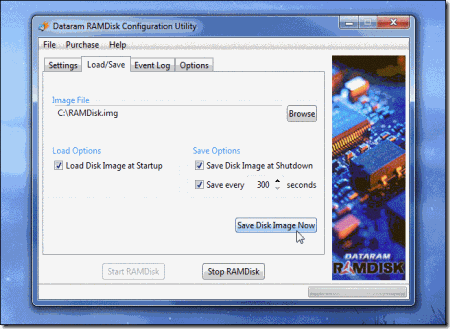
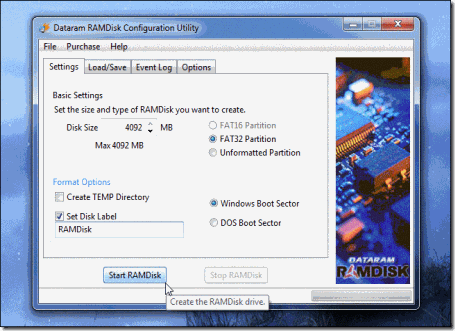
Making a RAM disk is pretty simple. Install a program like DataRAM’s RAMDisk Personal — the free version allows you to create RAM disks up to 4 GB in size — and use it to create a new RAM disk.
You can then install programs to it or move files to it. You’ll want to save a copy of the RAM disk so you won’t lose the data if your computer ever goes down. Of course you’ll have to save a new image every time you update the files on the RAM disk.
There Must Be Some Uses For a RAM Disk, But…
RAM disks aren’t a complete scam like PC cleaning programs and many other “system-optimization” tools are. It’s definitely faster to read and write from RAM rather than to use even a fast SSD. There are likely some good uses for RAM disks if you really know what you’re doing.
However, both of the following would have to be true:
· You’d have to be using a program doesn’t normally use RAM as a cache and instead insists on reading and writing small files to your hard drive.
· You’d have to not care about any of these files and have no problem if you lose them.
This is a high bar to clear — most programs that have a cache you don’t necessarily care about will use RAM, anyway. For example, there’s no point in placing Photoshop’s scratch file on a RAM disk because Photoshop uses RAM as a cache if it’s available. Your web browser will store its cache files in RAM if there’s space, too.
For programs that do write and read data from the hard drive, this data is likely something you don’t want to lose. Using a RAM disk with an important database would be a mistake because you’d lose the database if a crash or power loss occurred.
RAM-Based Solid-State Drives
If you do want to benefit from the speed of RAM, you may want to try investing in a RAM-based solid-state drive. These are solid-state drives that contain RAM instead of typical Flash memory. They’re much faster to read and write to, but also much more expensive because RAM is more expensive than Flash memory.
Such drives contain a battery, so they can maintain the contents of the RAM if the computer loses power. They have enough battery power to write the data to offline memory, ensuring you won’t lose whatever you stored in their RAM.
Such drives aren’t for the average user — they’re extremely expensive options intended for data centers and other business uses where you want the speed of RAM with the stability of SSDs. But these drives make much more sense than software RAM disks if you really need RAM-like speeds for mission critical purposes.
In summary, RAM disks do work as advertised. But you probably don’t want to use them, anyway. They’re not ideal for running an important database or speeding up game load times.
If you do have a smart use for a RAM disk, leave a comment — we’d like to know what people are actually using them for.
Taken From: http://www.howtogeek.com/171432/ram-disks-explained-what-they-are-and-why-you-probably-shouldnt-use-one/
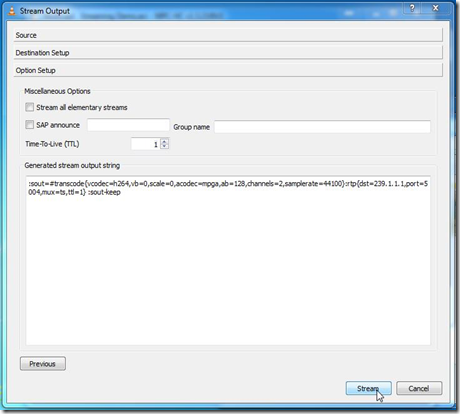
![[Multicast-realdemo.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgy8TnjoKFrLE-jDL5MEBuH_eO1JyEf_oWoRDOlZqcFY_ylBT9TsJRgVD9GH6L01718rwsC51K2bFFQqzrRWzrKuhF3b-eSn6oCKf4KOpZrnTLTFhsl50Hu79Yn09egyxfnmkhIfILqUXwB/s1600/Multicast-realdemo.jpg)