The Loopback Interfaces are very usefull to troubleshoot, it allows you to do test without using physical interfaces that may or may not be up. You can even shutdown manually / administratively a physical interface and enter it’s IP addresses on a loopback, and do your tests (like anouncing network via a dynamic routing protocol)
You can take the loopback interfaces and take them one step further, and make them part of the solution, and avoid having an extra routers, this is possible because the traffic goes in and out like it was entering and exiting another router.
In this example I will show you how to do NAT Overload to an IP different from the one in the WAN interface, this means that you will exit to the Internet with diferent Public IP from the one in the WAN interface. This is usefull for example when you want your guest wifi users to exit to the Internet with an Public IP that is different from the one the employes use.
Without NAT Overload on the Loopback (NAT Outside) you would have to implement a cenário like this: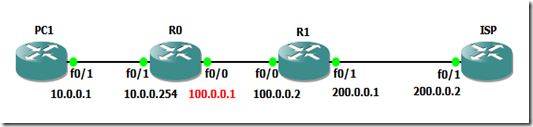
where you need an extra router (R0) to do the NAT Overload to the Public IP (100.0.0.1). Besides the aditional router you spend four Public IPs in the interconection between R0 and R1.
With NAT Overload on the Loopback interface you only need a cenário like this:
Below I will show you how to accomplish this in two ways:
- PBR with Set Next Hop – You also spend four Public IPs like in the cenario with a real router
- PBR with Set Inteface – You only spend one Public IP (the 100.0.0.1)
we use PBR to force the traffic we want to NAT with a different Public IP through to the Loopback Interface in order to get Nated. You could point the default route to the Loopback Interface, but when the traffic returned it wouldn’t be sent out through the WAN Interface (Fa0/1 on R1), It would be sent again to the Loopback.
NAT Overload on the Loopback - PBR with Set Next Hop
In this cenario we have a /30 Public IP in the Loopback this implies the following network:
- One IP for the network – 100.0.0.0
- One IP for R1 Loopback Interface (NAT Target) – 100.0.0.1
- One IP for the Next Hop (wich does not exist) - 100.0.0.2
- Once IP for Broadcast - 100.0.0.2
the IP for the Next Hop (100.0.0.2) at first glance look quite unuseful, but if you look PBR route map we use this IP even though it does not exist, because this forces the traffic to go out the Loopback (100.0.0.1) because it’s directly connected to the netwok (10.0.0.0/30) of the next hop set in the PBR route map.
## PC1 ###########################
hostname PC1
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 10.0.0.254
## ISP ###########################
hostname ISP
interface FastEthernet0/1
ip address 200.0.0.2 255.255.255.252
no shutdown
ip route 0.0.0.0 0.0.0.0 200.0.0.1
## R1 ############################
interface loopback 111
ip address 100.0.0.1 255.255.255.252
ip nat outside
no shutdown
interface FastEthernet 0/0
description *** LAN ***
ip address 10.0.0.254 255.255.255.0
ip nat inside
ip policy route-map Nat-Loopback
no shutdown
interface FastEthernet 0/1
description *** WAN ***
ip address 200.0.0.1 255.255.255.252
ip nat outside
no shutdown
access-list 102 remark *** Traffic for NAT Overload on The Loopback ***
access-list 102 permit ip 10.0.0.0 0.0.0.255 any
ip nat inside source list 102 interface loopback 111 overload
ip route 0.0.0.0 0.0.0.0 200.0.0.2
route-map Nat-Loopback permit 10
match ip address 102
set ip next-hop 100.0.0.2
## TEST ##########################
ISP# debug ip icmp
ISP# terminal monitor
PC1#ping 200.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 112/160/220 ms
PC1#
ISP#
*Mar 1 00:28:33.051: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.255: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.387: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.551: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.671: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
NAT Overload on the Loopback - PBR with Set Interface
In this cenario we have a /32 Public IP in the Loopback this implies the following network:
- One IP for R1 Loopback Interface (NAT Target) – 100.0.0.1
this achives the same result but using only one IP, and saving the other three for other usages.
In RED you have the changes from the previous cenario (PBR with Set Next Hop )
## PC1 ###########################
hostname PC1
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 10.0.0.254
## ISP ###########################
hostname ISP
interface FastEthernet0/1
ip address 200.0.0.2 255.255.255.252
no shutdown
ip route 0.0.0.0 0.0.0.0 200.0.0.1
## R1 ############################
interface loopback 111
ip address 100.0.0.1 255.255.255.255
ip nat outside
no shutdown
interface FastEthernet 0/0
description *** LAN ***
ip address 10.0.0.254 255.255.255.0
ip nat inside
ip policy route-map Nat-Loopback
no shutdown
interface FastEthernet 0/1
description *** WAN ***
ip address 200.0.0.1 255.255.255.252
ip nat outside
no shutdown
access-list 102 remark *** Traffic for NAT Overload on The Loopback ***
access-list 102 permit ip 10.0.0.0 0.0.0.255 any
ip nat inside source list 102 interface loopback 111 overload
ip route 0.0.0.0 0.0.0.0 200.0.0.2
route-map Nat-Loopback permit 10
match ip address 102
set interface loopback 111
%Warning:Use P2P interface for routemap set
interface clause
## TEST ##########################
ISP# debug ip icmp
ISP# terminal monitor
PC1#ping 200.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 200.0.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 112/160/220 ms
PC1#
ISP#
*Mar 1 00:28:33.051: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.255: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.387: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.551: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1
*Mar 1 00:28:33.671: ICMP: echo reply sent, src 200.0.0.2, dst 100.0.0.1




